By now, most of us know what DirectAccess is. For those who don’t, Direct Access is a revolutionary VPN technology which was introduced in Windows Server 2008 R2. It provides seamless connectivity to corporate resources without requiring any dial-up or VPN. DirectAccess connectivity is based on IPsec, IPV6, and transition technologies like Teredo, 6to4, IP-HTTPS, and ISATAP. In DirectAccess, the IPv6 traffic is encapsulated in an IPv4 packet and is then sent across the internet, after which the DirectAccess server reads the IPv6 headers and executes it.
Alright, so far we have understood that DirectAccess require IPv6, but what about the networks which aren’t ready yet for IPv6? It’s true that IPv6 is required for DirectAccess to work, but not natively. There are two ways to address this:
- Using ISATAP, this will automatically generate and assigns an IPv6 address to IPv6-capable machines internally. The DirectAccess server thus acts as an ISATAP router.
- Deploy Microsoft Unified Access Gateway (UAG) DirectAccess which uses NAT64 and DNS64 technologies to translate IPv4 to IPv6 and vice versa.
NAT64 and DNS64 are not present in the native Windows 2008 R2-based Direct Access solution because the communication is only possible between IPv6-aware machines.
Here’s how it works:
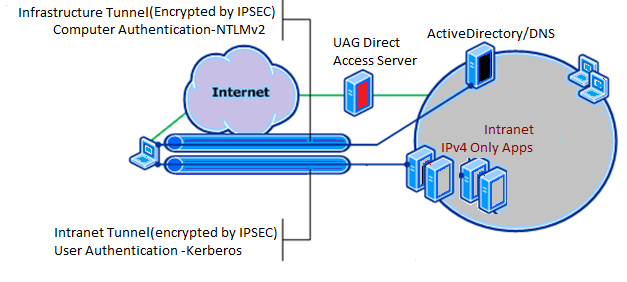
Let’s assume a user connected to DirectAccess, through the Microsoft UAG, tries to access a file share on a File server hosted internally. When the user types in \\fileshare and hits enter, the DirectAccess client machine checks the NRPT table (http://technet.microsoft.com/en-us/library/dd637795(WS.10).aspx#BKMK_NRPolicyTable) to verify where to send this request for a name resolution. If it’s supposed to be sent to the internal DNS Server, DirectAccess Client sends a DNS request for the resource to the UAG DirectAccess server. The DNS request is a AAAA (Quad A) query for getting the IPv6 address of the file server. When the UAG DirectAccess server gets this request, it simply queries a DNS server configured on its internal NIC for the HOST A record of the file server. The internal DNS server replies back with the IPv4 address, which is exactly similar to what would happen internally in an IPv4 network. This translation of AAAA to Host A that happens on the UAG DirectAccess Server is done by DNS64 technology.
The UAG server then creates a hash of the IPv4 address it received and adds it to the IPv6 suffix to create a dummy IPv6 address for the file server using NAT64 technology. It then forwards that IPv6 address to the client machine. The client machine sends another packet to the DirectAccess server with the received IPv6 address encapsulated in the IPv4 packet. UAG Server then receives the packet and retrieves the IPv6 headers. It translates the IPv6 to IPv4 and routes it normally through the corporate routers and switches. Both DNS64 and NAT64 technologies in the UAG are used to make the communication possible between the IPv6 and IPv4 enabled machines.
One thing to note here is that NAT64 and DNS64 are used only when the connection is initiated from a DirectAccess client machine, and not from an internal IPv4 machine.
Clearly, NAT64 and DNS64 play a vital role in DirectAccess connectivity and will continue to be an important facet until all networks operate solely on native IPv6.


